Vulnerability and Penetration Testing
Security is a worldwide issue, and individuals need more information and a framework that is more secure from danger and hacks. Every organization faces many vulnerabilities through which the hacker can get unauthorized access to its data.
We at GEC Certification is an experienced service provider for that related service of penetration testing. We have a dedicated team that helps us to maintain a sharp focus on the needs related topenetration testing. Our Penetration Testing services help to discover the vulnerabilities that would affect your network or system and also suggest ways to remove or lower the risk that can affect your business. We aim at providing outmost service quality, innovation, and research in the field of information security and technology.
We at Gec Certification have a set of qualified and experienced professional penetration testers that focuses on examining the IT systems and identify any weakness that can be used by attackers, which would disrupt the integrity and confidentiality of the associated data.
A proper penetration test is an important part of a full security audit. The Payment Card Industry Data Security Standard –PCI DSSneeds penetration testing on a regular schedule and after any system changes.

Why is it essential to have a Vulnerability Assessment?
The main aim of a vulnerability assessment is to help the organization to identify, quantify, and prioritize the technical vulnerabilities ina system and networks. It also helps to find the loopholes in their practices and policies. This is an efficient way to assess the business risk and to improve the security posture.
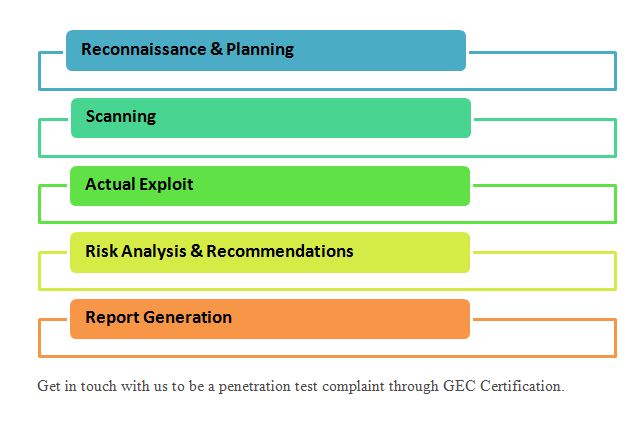
Phases of a penetration test
Penetration testers firstly begin by gathering information about the target. Then they identify the possible vulnerabilities that have affected the system by scanning. After the proper scanning, they launch the attack. Post attack, they analyze the vulnerabilities and the risk involved in the attack. The final step involves the detailed report submission summarizing the results of the penetration test.
Why is penetration testing important?
Penetration testing or pen test helps the organization in evaluating the security of a computer system.
It attempts to evaluate the security of the IT infrastructure by trying to exploit the vulnerabilities safely.
This testing enables us to find the gaps in the security tool that helps to find multiple attack vendors
This helps to ensure that proper controls have been implemented and that they are effective that offers assurance to IT and senior management teams.
The pens testing also helps to test the applications that are often the target of attacks, especially applications that are built by people who may have mistakes despite their best practices.
To identify and discover any new bugs that exist in the present software.
To understand and determine the weakness in the infrastructure (hardware), application (software) and people in order to develop controls
Pen testing is typically performed using the manual or automated technology that comprises of servers, web applications, network devices, mobile devices.
Vulnerabilities could be due to multiple reasons:
Any flaws in the design of the hardware and software
Poorly configured computer systems, applications, and networks
Usage of unsecured networks
Complex computer system architecture
Reasonable human errors